Zentyal 3.2 PPTP Server
Here is howto install Zentyal 3.2 PPTP Server. Since Zentyal 3.2 the developers have decided to remove the PPTP Server and now provide a more secured implementation together with L2TP and IPSec.
But as i can notice L2TP with IPSec is buggy and I’ve managed to fix the issue that i have but also decided to install PPTP Server and remove it after there is more stable release.
This example is for the Zentyal 3.2 Server installation which is using Ubuntu 12.04 LTS.
Install and configure the PPTP Server
Login as root and install the PPTP Server
sudo su apt-get install pptpd
My /etc/ppp/pptpd-options
name pptpd refuse-pap refuse-chap refuse-mschap require-mschap-v2 require-mppe-128 ms-dns <my Zentyal IP> proxyarp nodefaultroute debug lock nobsdcomp mtu 1200 mru 1200 plugin winbind.so ntlm_auth-helper '/usr/bin/ntlm_auth --helper-protocol=ntlm-server-1 --require-membership-of="MYDOMAIN\\VPN-Clients"'
The last two lines are for Authentication, this line will allow PPTP connections to all clinets that are members of my VPN-Clients group.
My /etc/pptpd.conf
option /etc/ppp/pptpd-options logwtmp bcrelay eth0 localip 192.168.0.170 remoteip 192.168.0.171-179
I’m using the bcrelay on my eth0 interface that is my internal LAN interface
Configure Zentyal Firewall
Now you need to allow traffic from your VPN clients to your local network. Create file /etc/zentyal/hooks/firewall.postservice and add your IP range to fnospoofmodules and inospoofmodules
vi /etc/zentyal/hooks/firewall.postservice
/sbin/iptables -t filter -A fnospoofmodules -s 192.168.0.171/32 -j faccept /sbin/iptables -t filter -A inospoofmodules -s 192.168.0.171/32 -j iaccept /sbin/iptables -t filter -A fnospoofmodules -s 192.168.0.172/32 -j faccept /sbin/iptables -t filter -A inospoofmodules -s 192.168.0.172/32 -j iaccept /sbin/iptables -t filter -A fnospoofmodules -s 192.168.0.173/32 -j faccept /sbin/iptables -t filter -A inospoofmodules -s 192.168.0.173/32 -j iaccept /sbin/iptables -t filter -A fnospoofmodules -s 192.168.0.174/32 -j faccept /sbin/iptables -t filter -A inospoofmodules -s 192.168.0.174/32 -j iaccept /sbin/iptables -t filter -A fnospoofmodules -s 192.168.0.175/32 -j faccept /sbin/iptables -t filter -A inospoofmodules -s 192.168.0.175/32 -j iaccept /sbin/iptables -t filter -A fnospoofmodules -s 192.168.0.176/32 -j faccept /sbin/iptables -t filter -A inospoofmodules -s 192.168.0.176/32 -j iaccept /sbin/iptables -t filter -A fnospoofmodules -s 192.168.0.177/32 -j faccept /sbin/iptables -t filter -A inospoofmodules -s 192.168.0.177/32 -j iaccept /sbin/iptables -t filter -A fnospoofmodules -s 192.168.0.178/32 -j faccept /sbin/iptables -t filter -A inospoofmodules -s 192.168.0.178/32 -j iaccept /sbin/iptables -t filter -A fnospoofmodules -s 192.168.0.179/32 -j faccept /sbin/iptables -t filter -A inospoofmodules -s 192.168.0.179/32 -j iaccept exit 0
Don’t forget the exit 0 at the end.
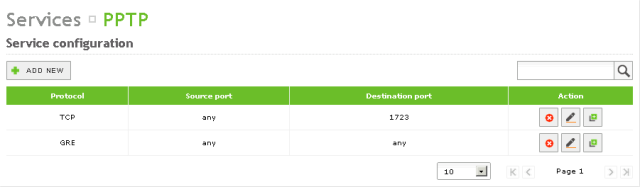
Now we need to allow PPTP traffic to our Zentyal Server. Go to Network -> Services and Add new PPTP Service with TCP 1723 and GRE protocol
Now Allow the traffic on the WAN interfaces. Go to Firewall -> Packet Filter -> Filtering rules from external networks to Zentyal and add the PPTP service
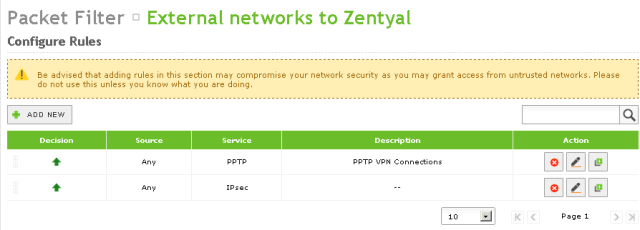
With this configuration you will be able to have PPTP clients connect to your Zentyal 3.2 Server and to enable client to connect just add him to VPN-Clients group.
Zentyal: http://www.zentyal.org/






How to access Zentyal through RDP. *Note*: this method is provided for reference only, and is not intended as a supported method of accessing Zentyal desktop interface. Use at your own risk. Question: How can I access Zentyal Server graphic environment using an RDP client (i.e. Windows Remote Desktop or Vinagre)? Answer: In order to access Zentyal through Remote Desktop Protocol, first we should install the xrdp daemon: sudo apt-get install xrdp Check that this should install, apart from xrdp, tightvncviewer server. In some scenarios, however, it installs vnc4server, or does not install any of these becausevnc4server is already installed.… Read more »
Why adding identical rules so many times ?
/sbin/iptables -t filter -A fnospoofmodules -s 192.168.0.179/32 -j faccept
/sbin/iptables -t filter -A inospoofmodules -s 192.168.0.179/32 -j iaccept
it’s because I’ve added all the IP’s that i use for my PPTP connections in /etc/pptpd.conf:
remoteip 192.168.0.171-179
Regards
Nick, This is an awesome post. Everything work for me the first time. You are the man.
hello, is this the same when adding pptp to zentyal 4.0 ?
Hello Manel,
I haven’t tested it but it should work because I’m using the linux pptpd package and adding firewall rules so the server will not block the PPTP traffic.
Regards,
Nikola
Hello Nikola,
I do need your help please , when i modify /etc/ppp/pptpd-options and /etc/pptpd.conf
it is impossible to save them because i have not the right it is read only . I tried to modify the right with this cmd ( chmod u+w /etc/ppp/pptpd-options) and i failed also. I have copied it and created a new file containing the file and i failed too . What should i do .Thank you for answering
2016-03-17 8:44 GMT+01:00 lahmar manel:
type: sudo su
enter your password and you will be logged in as root, then you will be able to change the file
Regards,
NIkola
Hello Nikola,
I can’t do it . Did you meant by “you will be able to have PPTP clients connect to your Zentyal 3.2 Server and to enable client to connect just add him to VPN-Clients group” i tried but i failed what should i do . I do really need your help please.