Mikrotik to Cisco ASA IPsec VPN
We needed to setup IPsec VPN for a client with a remote location that already had Cisco ASA. So, here is a Mikrotik to Cisco ASA IPsec howto.
Tutorial Scenario
Cisco ASA site
- WAN: 1.1.1.2/30 (outside)
- LAN: 192.168.2.1/24 (inside)
Mikrotik site
- WAN: 1.1.1.1/30 (ether1)
- LAN: 192.168.1.1/24 (ether2)
Cisco ASA to Mikrotik configuration
Launch the VPN configuration wizard on your Cisco ASA router
Set VPN Tunnel Type as Site-to-Site
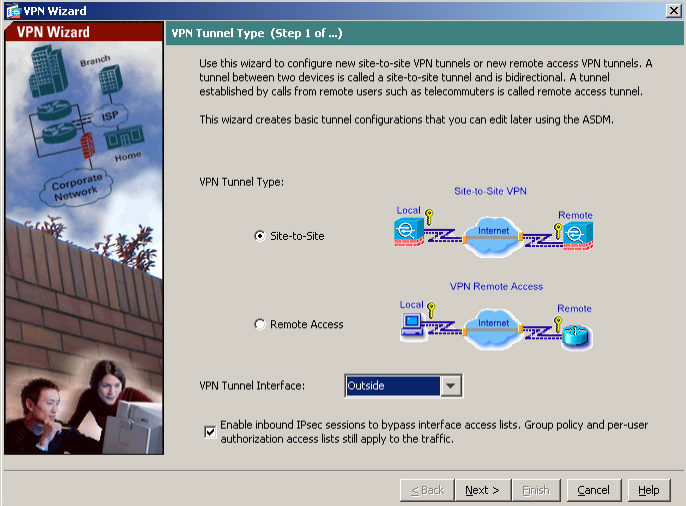
Set the Remote Peer IP Address: 1.1.1.1(Mikrotik WAN) and Pre-shared key. Also Tunnel Group Name should be the Remote Peer IP Address.
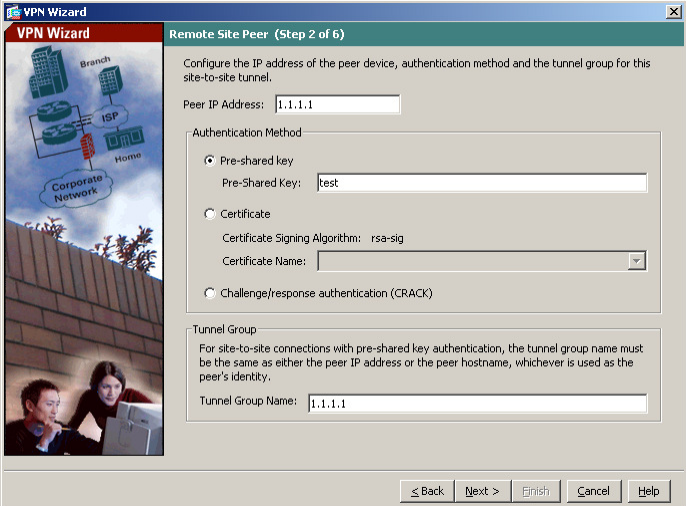
Set the IKE Policy Encryption to 3DES, Authentication to MD5 and DH Group to 2
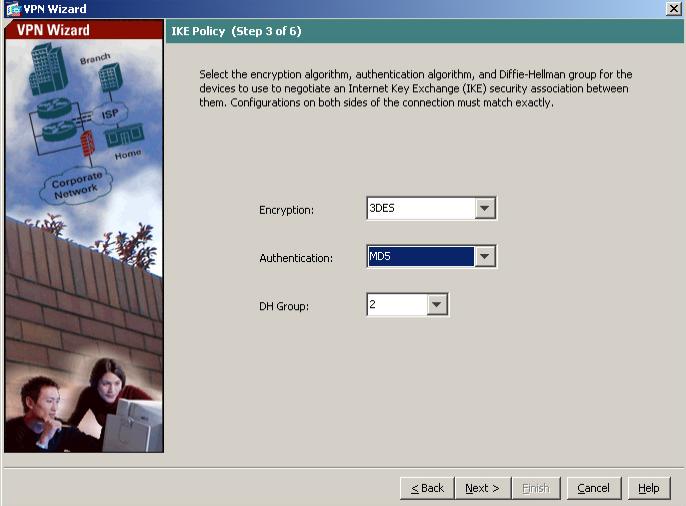
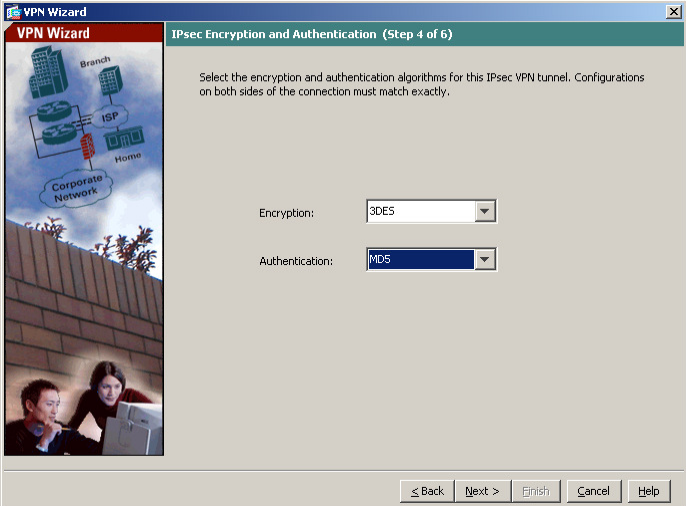
Set the IPsec Encryption to 3DES and Authentication to MD5
Set the Local and Remote Networks
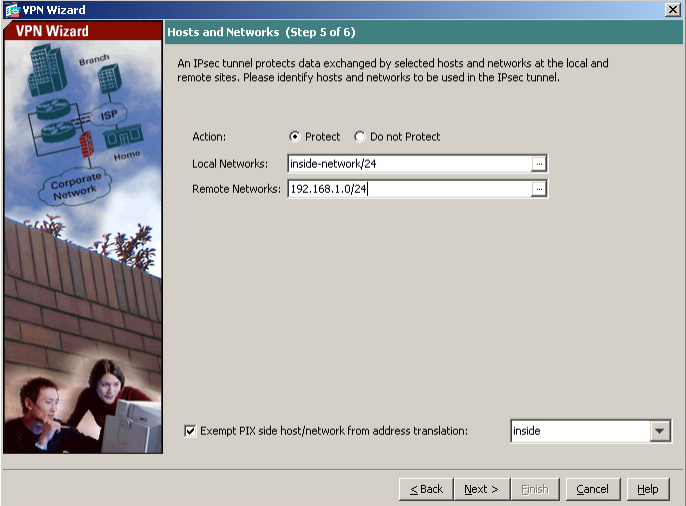
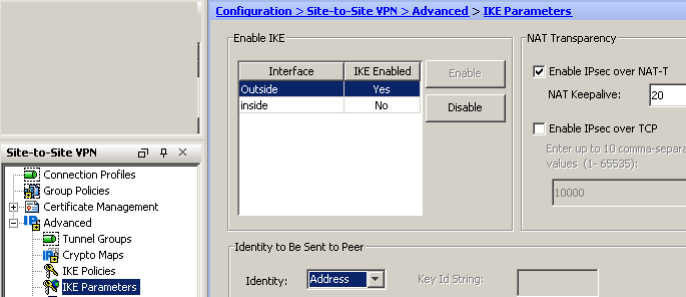
Don’t forget to set the IKE Parameters to Identity: Address to avoid connection problems
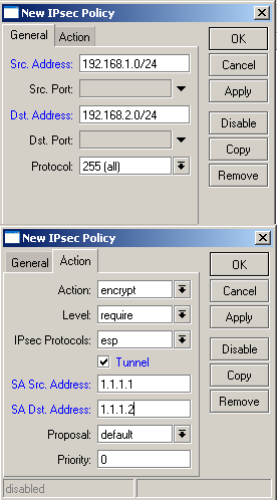
Mikrotik to Cisco ASA configuration
Create new policy
Create new Peer
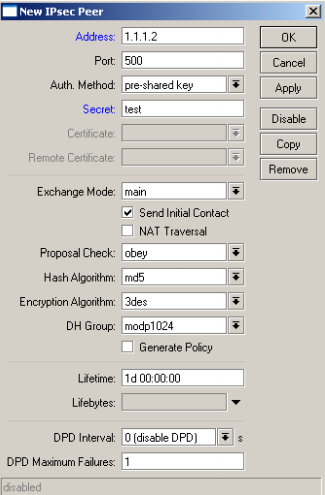
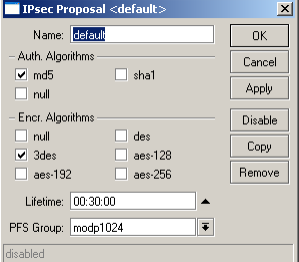
Modify the default proposal to accept MD5 as Authentication
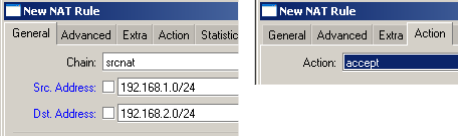
Create NAT rule to bypass the traffic that should to trough the tunnel
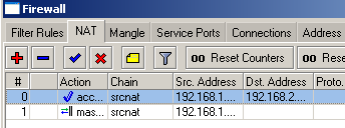
Move the rule to the top
Now you can connect your branch offices using Mikrotik Routers even if you have Cisco ASA’s installed on the other locations.
Links: Cisco ASA, Mikrotik Routerboard









Mnogu dobar blog , povekje od korisen :) , bravo za Mrki.
Многу добар блог, Фала ти многу за сценариово, работи :) Поздрав
You saved my day – thank you! :)
Good post
Good job
Didn’t work for me.
check if PFS enabled or disabled and the the encryption. MD5 is getting removed from the new Cisco devices.I haven’t checked Mikrotik’s default proposals on the latest RouterOS.
It should work.
Great article! Thank you very much!
Worked for me after enabling PFS in ASA!
Also, I used SHA instead of MD5
Hi,Thank you,it helped me a lot,but i connected site to site IPSec between juniper and Mikrotik.
Hello, I consulted, so configure as itemize the mikrotik and handle the other side, behind the handle is where these equipment I need to connect, the problem I have to shoot from the ASA a ‘packet-tracert “tool for the mikrotik the ipsec vpn connects, has any idea what is happening?
I from him tug mikrotik lan ping but I can not activate the vpn on the handle. Thank You
im connected with ip sec but trafic not work
From the Mikrotik try to ping the ASA private IP to see if you have NAT issues or something else.
If you can ping the ASA private IP then see if your NAT bypass rule is above your masquerade rule as shown on the last picture.
Regards,
Nikola
Hi, I have similar requirement. at some remote site Cisco ASA is running, they have provided us with vpn client dialer which we uses from our windows base pc to connect to there site. Now i want to connect my mikroitk. I have not control over there ASA and they have not provided us much details. all details i have gathered via vpn dialer. How i achieve the task to conenct mikrotik to remote asa ?
Niko, is it possible to enable traffic from ASA LANs to LAN behind Mikrotik in this configuration? We have similar IPsec configs with Fortigate routers and it works with them fine, but not with Mikrotik. Is it necessary to make ip-ip tunnel?